Security is often defined as the state of being free from danger or threat. But what does this mean in practice? What does it imply to be free from danger? Is it the same in enterprise and industrial systems? Well, short answer: no, it's not. Several reasons but one important is that the underlying technological architectures for each one of these environments, though shares technical bits, are significantly different which leads to a different interpretation of what security (again, being free from danger and threats) requires.
This short essay analyzes some of the cyber security aspects that apply in different domains including IT, OT, IoT or robotics and compares them together. Particularly, the article focuses on clarifying how robotics differs from other technology areas and how a lack of clarity is leading to leave the user heavily unprotected against cyber attacks. Ultimately, this piece argues on why cyber security in robotics will be more important than in any other technology due to its safety implications, including IT, OT or even IoT.
Introducing some common terms
Over the years, additional wording has developed to specify security for different contexts. Generically, and from my readings, we commonly refer to cyber security (or cybersecurity, shortened as just "security") as the state of a given system of being free from cyber dangers or cyber threats, those digital. As pointed out, we often mix "security" associated with terms that further specify the domain of application, e.g. we often hear things such as IT security or OT security.
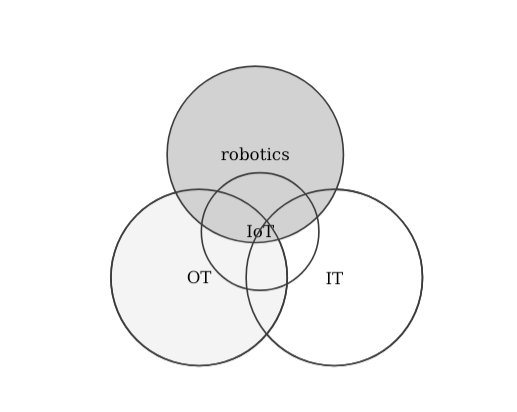
During the past two years, while reading, learning, attending to security conferences and participating on them, I've seen how both security practitioners and manufacturers caring about security do not clearly differentiate between IT, OT, IoT or robotics. Moreover, it's often a topic for arguments the comparison between IT and IT security. The following definitions aim to shed some light into this common topic:
- Information Technology (IT): the use of computers to store, retrieve, transmit, and manipulate data or information throughout and between organizations[1].
- Operational Technology (OT): the technology that manages industrial operations by monitoring and controlling specific devices and processes within industrial workflows and operations, as opposed to administrative (IT) operations. This term is very closely related to:
- Industrial Control System (ICS): is a major segment within the OT sector that comprises those systems that are used to monitor and control the industrial processes. ICS is a general term that encompasses several types of control systems (e.g. SCADA, DCS) in industry and can be understood as a subset of OT.
- Internet of the Things (IoT): an extension of the Internet and other network connections to different sensors and devices — or "things" — affording even simple objects, such as lightbulbs, locks, and vents, a higher degree of computing and analytical capabilities. The IoT can be understood as an extension of the Internet and other network connections to different sensors and devices.
- Industrial Internet of the Things (IIoT): refers to the extension and use of the Internet of Things (IoT) in industrial sectors and applications.
- robotics: A robot is a system of systems. One that comprises sensors to perceive its environment, actuators to act on it and computation to process it all and respond coherently to its application (could be industrial, professional, etc.). Robotics is the art of system integration. An art that aims to build machines that operate autonomously.
Robotics is the art of system integration. Robots are systems of systems, devices that operate autonomously.
It's important to highlight that all the previous definitions refer to technologies. Some are domain specific (e.g. OT) while others are agnostic to the domain (e.g. robotics) but each one of them are means that serve the user for and end.
Comparing the security across these technologies
Again, IT, OT, ICS, IoT, IIoT and robotics are all technologies. As such, each one of these is subject to operate securely, that is, free from danger or threats. For each one of these technologies, though might differ from each other, one may wonder, how do I apply security?
Let's look at what literature says about the security comparison of some of these:
From [2]:
Initially, ICS had little resemblance to IT systems in that ICS were isolated systems running proprietary control protocols using specialized hardware and software. Widely available, low-cost Ethernet and Internet Protocol (IP) devices are now replacing the older proprietary technologies, which increases the possibility of cybersecurity vulnerabilities and incidents. As ICS are adopting IT solutions to promote corporate connectivity and remote access capabilities, and are being designed and implemented using industry standard computers, operating systems (OS) and network protocols, they are starting to resemble IT systems. This integration supports new IT capabilities, but it provides significantly less isolation for ICS from the outside world than predecessor systems, creating a greater need to secure these systems. While security solutions have been designed to deal with these security issues in typical IT systems, special precautions must be taken when introducing these same solutions to ICS environments. In some cases, new security solutions are needed that are tailored to the ICS environment.
While Stouffer et al. [2:1] focus on comparing ICS and IT, a similar rationale can easily apply to OT (as a superset of ICS).
To some, the phenomenon referred to as IoT is in large part about the physical merging of many traditional OT and IT components. There are many comparisons in literature (e.g. [3] an interesting one that also touches into cloud systems, which I won't get into now) but most seem to agree that while I-o-T aims to merge both IT and OT, the security of IoT technologies requires a different skill set. In other words, the security of IoT should be treated independently to the one of IT or OT. Let's look at some representations:
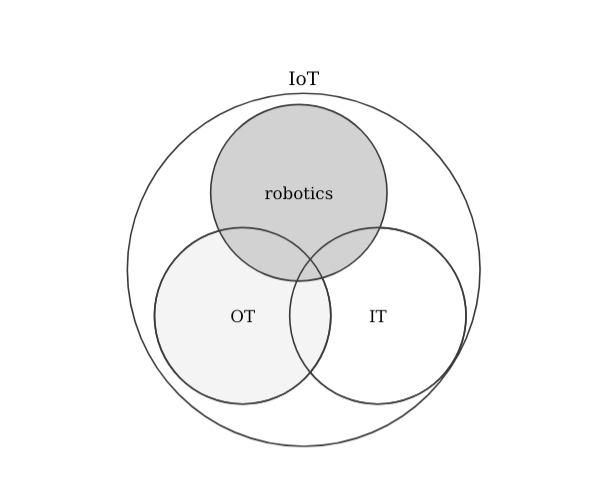
What about robotics then? How does the security in robotics compare to the one in IoT or IT? Arguably, robotic systems are significantly more complex than the corresponding ones in IT, OT or even IoT setups. Shouldn't security be treated differently then as well? I definitely believe so and while much can be learned from other technologies, robotics deserves its own security treatment. Specially because I strongly believe that:
cyber security in robotics will be more important than in any other technology due to its safety implications, including IT, OT or even IoT.
Of course, I'm a roboticist so expect a decent amount of bias on this claim. Let me however further argue on this. The following table is inspired by processing and extending [2:2] and [4] for robotics while including other works such as [3:1], among others:
| Security topic | IT | OT (ICS) | I(I)oT | Robotics |
|---|---|---|---|---|
| Antivirus | widely used, easily updated | complicated and often imposible, network detection and prevention solutions mostly | Similarly complicated, lots of technology fragmentation (different RTOSs, embedded frameworks and communication paradigms), network detection and prevention solutions exist | complicated and complex due to the technology nature, very few existing solutions (e.g. RIS), network monitoring and prevention isn't enough due to safety implications |
| Life cycle | 3-5 years | 10-20 years | 5-10 years | 10+ years |
| Awareness | Decent | Poor | Poor | None |
| Patch management | Often | Rare, requires approval from plant manufacturers | Rare, often requires permission (and/or action) from end-user | Very rare, production implications, complex set ups |
| Change Management | Regular and scheduled | Rare | Rare | Very rare, often specialized technitians |
| Evaluation of log files | Established practice | Unusual practice | Unusual practice | Non-established practice |
| Time dependency | Delays Accepted | Critical | Some delays accepted (depends of domain of application, e.g. IIoT might be more sensitive) | Critical, both inter and intra robot communications |
| Availability | Not always available, failures accepted | 24*7 | Some failures accepted (again, domain specific) | 24*7 available |
| Integrity | Failures accepted | Critical | Some failures accepted (again, domain specific) | Critical |
| Confidentiality | Critical | Relevant | Important | Important |
| Safety | Not relevant (does not apply generally) | Relevant | Not relevant (though depends of domain of application, but IoT systems are not known for their safety concerns) | Critical, autonomous systems may easily compromise safety if not operating as expected |
| Security tests | Widespread | Rare and problematic (infrastructure restrictions, etc.) | Rare | Mostly not present (first services of this kind for robotics are starting to appear) |
| Testing environment | Available | Rarely available | Rarely available | Rare and difficult to reproduce |
| Determinism requirements (refer to [5] for definitions) | Non-real-time. Responses must be consistent. High throughput is demanded. High delay and jitter may be acceptable. Less critical emergency interaction. Tightly restricted access control can be implemented to the degree necessary for security | Hard real-time. Response is time-critical. Modest throughput is acceptable. High delay and/or jitter is not acceptable. Response to human and other emergency interaction is critical. Access to ICS should be strictly controlled, but should not hamper or interfere with human-machine interaction | Often non-real-time, though some environment will require soft or firm real-time | Hard real-time requirements for safety critical applications and firm/soft real-time for other tasks |
Looking at this table and comparing the different technologies, it seems reasonable to admit that robotics receives some of the heaviest restrictions when it comes to the different security properties, certainly, much more than IoT or IT.
Still, why do robotic manufacturers focus solely on IT security?
A misunderstanding that users are paying heavily in robotics
As pointed out, it's not few that misunderstand IT security with robotics security. One of the best examples I've recently seen is how Mobie Industrial Robots (MiR) engineering team (lead members!) care only about IT security, though I've repeatedly indicated them that this is a mistake and they should have a wider perspective of what security aspects they should consider when dealing with robotics technology:


Since they indicated IT security, one would expect them to care also for OT (since these robots operate on many industrial scenarios), however there's none. There are no sections for OT security and much less, a proper threat modeling that fits security to this particular robotic technology. None.
Knowing that sources like [6] already mix up IT security with cyber security, overall, I've spent decent amount of time (and meetings) to explain the difference, highlight the importance of caring about security holistically and convincing some managers and decision makers in robotics about this (including MiR!).
MiR presents one of the several examples out there of how a lack of concern, care and understanding of security for robotics is making end users exposed to hazards. Similar to MiR, other companies including Universal Robots (UR) or Teradyne (matrix of both MiR and UR) don't seem to really care about security and for now, continue profiting their insecure supply chain.
Safety hazards in robotics don't just impact privacy (as in IT), a compromised robot can damage humans and the environment. End users should demand a minimum of security from robot manufacturers. Action must be taken now by manufacturers and they should pro-actively invest in securing their systems.
Information technology. (2020). Retrieved June 23, 2020, from https://en.wikipedia.org/wiki/Information_technology. ↩︎
Stouffer, K., Falco, J., & Scarfone, K. (2011). Guide to industrial control systems (ICS) security. NIST special publication, 800(82), 16-16. ↩︎ ↩︎ ↩︎
Atlam, Hany & Alenezi, Ahmed & Alshdadi, Abdulrahman & Walters, Robert & Wills, Gary. (2017). Integration of Cloud Computing with Internet of Things: Challenges and Open Issues. 10.1109/iThings-GreenCom-CPSCom-SmartData.2017.105. ↩︎ ↩︎
TUViT, TÜV NORD GROUP. Whitepaper Industrial Security based on IEC 62443 https://www.tuvit.de/fileadmin/Content/TUV_IT/pdf/Downloads/WhitePaper/whitepaper-iec-62443.pdf ↩︎
Gutiérrez, C. S. V., Juan, L. U. S., Ugarte, I. Z., & Vilches, V. M. (2018). Towards a distributed and real-time framework for robots: Evaluation of ROS 2.0 communications for real-time robotic applications. arXiv preprint arXiv:1809.02595. ↩︎
Computer security. (2020). Retrieved June 23, 2020, from https://en.wikipedia.org/wiki/Computer_security. ↩︎
